 WARNING: This article contains absolutely nothing whatsoever to do with firearms, but has everything to do with not being victimized by the bad guys who use the very technology we use on a daily basis to attack us. Last week, I had the opportunity to attend the 2012 Rocky Mountain Information Security Conference (RMISC), which was hosted by the Denver chapter of ISACA and the Information Systems Security Association. One of the breakout sessions I attended was Georgia Weidman’s talk on the glaring need for smart phone security. Besides leaving with the thought “…what ever happened to the day when these things were JUST phones?!” I was reminded of the fact that with the added technology and functionality, our “phones” need to be protected just as do our computers.
WARNING: This article contains absolutely nothing whatsoever to do with firearms, but has everything to do with not being victimized by the bad guys who use the very technology we use on a daily basis to attack us. Last week, I had the opportunity to attend the 2012 Rocky Mountain Information Security Conference (RMISC), which was hosted by the Denver chapter of ISACA and the Information Systems Security Association. One of the breakout sessions I attended was Georgia Weidman’s talk on the glaring need for smart phone security. Besides leaving with the thought “…what ever happened to the day when these things were JUST phones?!” I was reminded of the fact that with the added technology and functionality, our “phones” need to be protected just as do our computers.
Specific Dangers: Your smart phone does not just contain your contact list. Many people are using their smart phones to receive email, store documents, input calendar items, keep notes, store passwords, and various other useful things. So these devices now hold all kinds of potentially sensitive personal data that must be protected. If a piece of malicious software (malware) gets installed on your phone, it can steal this data and send it off to the bad guys without you even knowing about it. The SMS (text message) functionality, along with the Internet connectivity features, on these devices are often leveraged vehicles for “exfiltrating” your sensitive data.
Not only is your personal data at risk, but also other information, such as your phone’s identity (the information that uniquely identifies your phone on the network), your geographical location, and information about the hardware and storage on your device can be disclosed. According to Ms. Weidman, the International Mobile Equipment Identification (IMEI) number that uniquely identifies your phone is as valuable to the bad guys as a credit card number, as this number is used by various apps to identify the smart phone as being yours when it logs on to the service. GPS information is also used to identify where you are located when using the services that you are accessing with your phone. Your phones can also connect to mobile WiFi hotspots, which means that they are as vulnerable to attack by malicious hotspots near your local coffee shop (disguising as legitimate hotspots) as is your laptop. Be careful about the networks you are connecting to.
So what can you do? Two things that really stuck out from this presentation, in terms of minimizing risks and ensuring better personal security, were the need for: 1) Having a security suite installed on your smart phone, and 2) Be careful what you download, and what permissions are being asked for.
Smart-Phone Security Software: In case you weren’t aware of this already, there are various apps out there that will help provide added security for your smart phone device. The problem is, however, that the tradeoff for additional security is often reduced performance. Do some research and find out which security suites have better reviews. I use the Norton Mobile Security Suite for my Android, and so far I haven’t noticed any huge or unbearable performance hits. Even the “lite” version will give you basic malware protection, but you can get additional features in the paid version for remotely wiping or locking your phone if it is lost or stolen. This is kind of a cool feature – I set up my spouse’s phone as a “buddy” so that if my phone is stolen or lost, I can send commands to my phone remotely. For example, if her specific phone number sends a “wipe” command to my phone, along with a password, I can wipe my phone remotely and erase all of my sensitive data.
There are various other security suites out there such as Avast, Kaspersky, and Lookout. Take a look at the links, do some research and find out which ones have the features you need and the performance you want. Each link gives reviews to help you see what others are saying about each product.
Application Security: If ever there was a need to read the fine print, reading those permissions that your new apps are asking for is it. When you download a new app for a smart phone, the app will often tell you what permissions it needs in order to operate. Every time you download a new app, go ahead and read that list of permissions and take note of what that app needs to access in order to function properly. Here is a good article that further explains permissions and how you can get more information about each permission that is being asked for when you install an app.
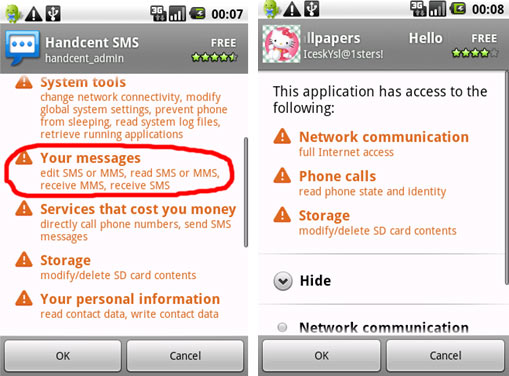
Sample Android App Permissions
Smart phone security is every bit as important to keeping you from being an online victim as is protecting your computer. In the coming weeks, I will take a look at some additional ways to stay safe by addressing specific smart phone issues. It's up to you to Refuse to be a Victim!
Additional Resources:
About The Author: "The Gonz" is an NRA Certified Firearms Instructor (Pistol, PPiTH, RTBAV), US Concealed Carry Association Affiliate Instructor, and an NRA Certified Range Safety Officer. Additionally, he a trained and certified Community Emergency Response Team (CERT) member, with several years of training in the Incident Command System (ICS) procedures and practices.

